Cyclic Redundancy Check Cyclic Redundancy Check is a data-based calculation of a set of test codes that are used to check whether data transmission has been changed or transmitted incorrectly.
Principle of algorithmAssume that the 15-bit binary information g=101001110100001 needs to be transmitted during data transmission. This binary code can be expressed as an algebraic polynomial g(x) = x^14 + x^12 + x^9 + x^8 + x^7 + x^5 + 1, where the value of the kth bit in g corresponds to the coefficient of x^k in g(x). Multiply g(x) by x^m, and add m zeros to g, then divide by m-order polynomial h(x) to get the binary code r corresponding to the residue m(m-1) term r(x). It is the CRC code.
h(x) can be freely selected or use an international prevailing standard. Generally, the CRC algorithm is called CRC-m according to the order m of h(x), such as CRC-32, CRC-64, and the like.
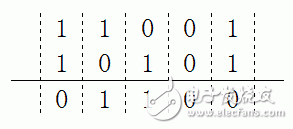
The division of g(x) and h(x) can be done by g and h as xor (exclusive OR) operations. For example, do 11001 and 10101 xor operation:
After understanding the xor algorithm, an example uses the CRC-8 algorithm to find the validation code of 101001110100001. In the CRC-8 standard, h(x) = x^8 + x^7 + x^6 + x^4 + x^2 + 1, where h is a 9-bit binary string 111010101.
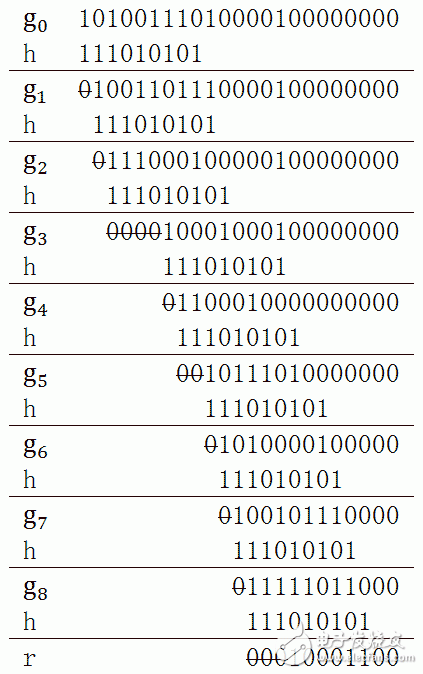
After iterative operations, the resulting r is 10001100, which is the CRC test code.
By way of example, you can find some rules and adjust the algorithm based on these rules:
1. At each iteration, b is determined according to the first position of gk, and b is the binary code to be used for operation with gk. If the first position of gk is 1, then b=h; if the first position of gk is 0, then b=0, or skip this iteration. In the above example, it will jump to the following non-zero position after encountering 0.
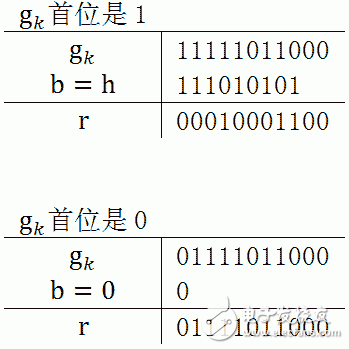
2. Each iteration, the first position of gk will be removed, so you only need to consider the second bit and calculate it. In this way, the first position of h can be discarded, and b is taken as the m position of h. For example, the h of the CRC-8 is 111010101, and the b is only 11010101.
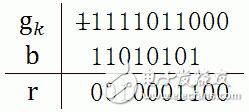
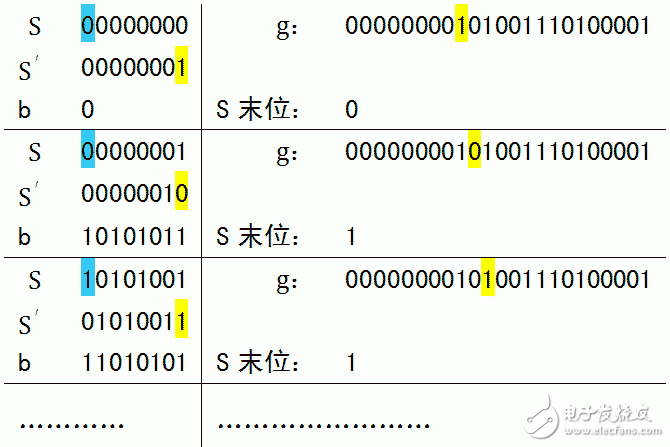
3. Each iteration is affected by the first m bits of gk, so an m-bit register S is built, which stores the first m bits of gk. The first bit of S is discarded before each iteration calculation, the register is shifted left by one, and the last bit of g is added to the register. If you use this method, the calculation steps are as follows:
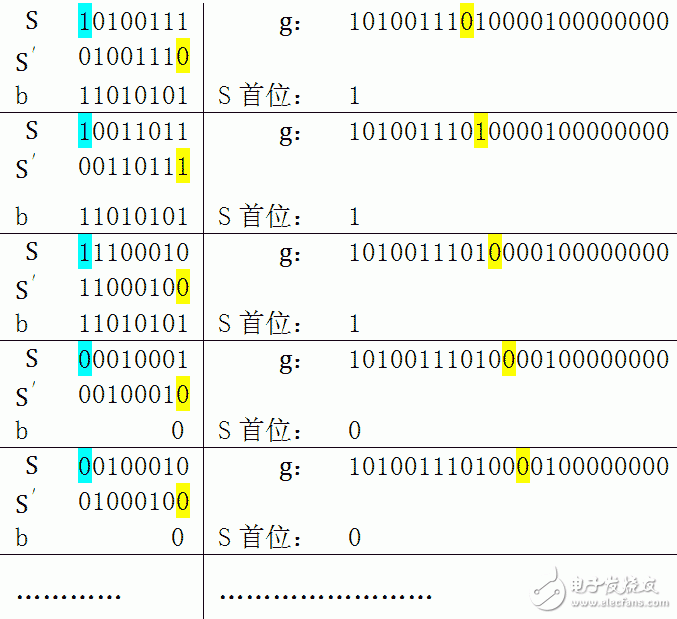
※ Blue indicates the top of the register S, which needs to be removed. b selects 0 or h according to the first position of S. Yellow is the bit that needs to be shifted into the register. S' is the displaced S.
Look-up table
Also in the above example, the data is organized into blocks of 4 bits each, so that g is divided into 6 blocks.
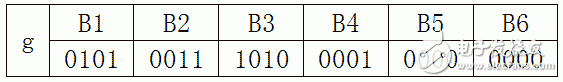
The following table shows the four iterative calculation steps. The gray background bits are stored in registers.
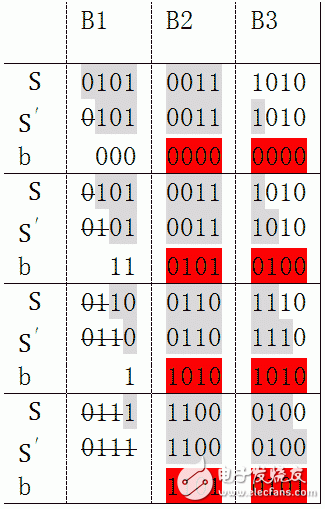
After 4 iterations, B1 is shifted out of the register. The part that was removed is not what we care about. What we care about is what effect these four iterations have on B2 and B3. Note the red part of the table, first defined as follows:
B23 = 00111010
B1 = 00000000
B2 = 01010100
B3 = 10101010
B4 = 11010101
b' = b1 xor b2 xor b3 xor b4
The 4 iterations for B2 and B3 are actually to make xor calculations with b1, b2, b3, b4, both:
B23 xor b1 xor b2 xor b3 xor b4
It can be proved that the xor operation satisfies commutative and associative laws, so:
B23 xor b1 xor b2 xor b3 xor b4 = B23 xor (b1 xor b2 xor b3 xor b4) = B23 xor b'
B1 is determined by the first bit of B1, b2 is decided by the second bit after the iteration of B1 (which is determined by the first and second bits of B1). Similarly, both b3 and b4 are determined by B1. B' can be calculated through B1. In addition, B1 consists of 4 bits, of which there are 2^4 possible values. So we can think of a faster algorithm, in advance of b' all possible values, 16 values ​​can be seen as a table; so you can not have to do that 4 iterations, but use B1 lookup table to get b' value , move B1 out, B3 move in, calculate with b', then the next iteration.
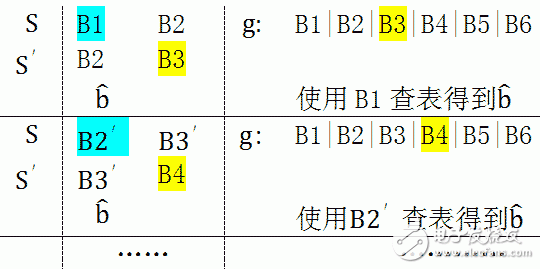
It can be seen that in each iteration, the data in the register is shifted in and out in units of 4 bits. The key is to obtain the register through the first 4 bits of the register.
, Such an algorithm can greatly increase the speed of operation.
The above method is a semi-byte lookup table method. There are also single-byte and double-byte look-up tables. The principles are the same. The possible values ​​of 2^8 or 2^16 b' are calculated in advance. Iterations The use of the register before the 8-bit or 16-bit lookup table to obtain b'.
Reverse algorithm
The previously discussed algorithm can be referred to as the forward CRC algorithm, meaning that the left bit of g is considered as a high bit and the right bit is considered as a low bit. The right side of G adds m zeros, and then iterative calculations start from the upper bits and gradually add the lower bits to the registers. In the actual data transmission process, the CRC code is calculated while receiving data, and the forward algorithm regards the newly received data as a low bit.
The reverse algorithm, as its name suggests, treats the left data as low, and the right data as high. In this case, we need to add m zeros to the left of g, and h should also be reversed. For example, the forward CRC-16 algorithm h=0x4c11db8 and the inverse CRC-16 algorithm h=0xedb88320. The choice of b is 0 or h, which is determined by the first bit on the right of the register, not the first bit on the left. The register is still shifted to the left, which means that the iteration becomes low to high.
Benefits of Privacy Screen Protectors
As a personal item, a mobile phone will always contain all kinds of private information and secrets. Therefore, when many people use their mobile phones in public places, they are worried that their screen content will be seen by the people next to them. Especially when you use your mobile phone to enter various passwords, it is very dangerous if you are targeted by malicious people.
In order to prevent private information and confidential documents from being peeped, Privacy Screen Protector came into being. As the name suggests, it is a Mobile Phone Screen Protector, which can prevent others from prying on the screen and protect personal privacy. When you install a Privacy Screen Protector on your phone, people around you won't be able to see what's on your screen.
The Anti-Spy Screen Protector uses patented ultra-fine louver optical technology, so that the information on the screen is displayed on the front for the user to read. The viewable area is 60 degrees. Anyone can only see the dark picture on both sides. And the anti-blue light effect of the Privacy Screen Protective Film, the blue light blocking rate is about 10%-30%, and the mobile phone with the Privacy Film will automatically darken to reduce some glare. Therefore, normal use will not hurt the eyes, but will play a protective role. Anti-peeping Screen Protector effectively protect business secrets and personal privacy. Whether it is work, study, communication or entertainment, it makes the use of computers and mobile phones more free. Help the company's senior business personnel, lawyers, consultants, financial personnel, etc. to avoid screen information leakage when using mobile phones.
Anti-Peep Hydrogel Screen Protector,Anti-Spy Tpu Hydrogel Film,Privacy Hydrogel Protector,Privacy Screen Protector Sheet
Shenzhen TUOLI Electronic Technology Co., Ltd. , https://www.szhydrogelprotector.com