We all know that Windows 10 uses stricter rights protection. For system protection programs and file (folder) reads, many times when we log in as an administrator, we do not have the appropriate permissions to read or change. So how do you circumvent the restrictions on permissions without affecting system security?
Bypassing UAC restrictions, run as Administrator
Use tools: runas command line
Windows 10 defaults to the UAC limit. If you run a program that reads or changes the system settings, the system will pop up the UAC interception prompt. We must click Yes to confirm the operation. UAC can well protect the security of the system, but some programs that are confirmed to be safe are registry editors, command prompts, and we don't want UAC interception when running these programs. The usual method is to close the UAC prompt, or log in directly using the Administrator account, but these operations will bring security risks to the system. How can you bypass the UAC restrictions without affecting system security? We only need to run the specified program as Administrator.
First open the computer management tools, expand the "System Tools → Local Users and Groups", select the right side of the Administrator account opens, switch to "General", and then remove the "Account is disabled" check, enable the account, and set for it A complicated password (Figure 1).
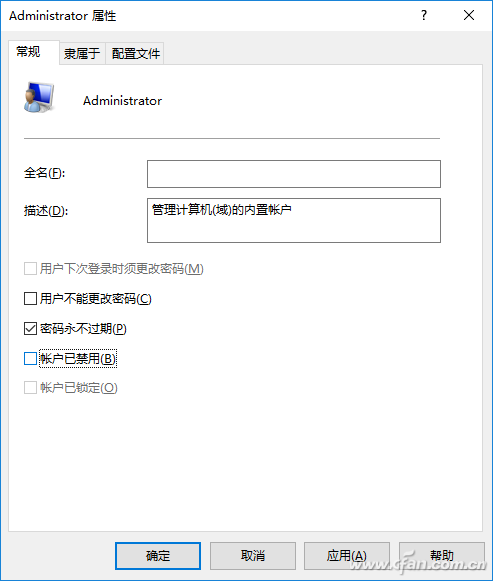
Figure 1 Activate Account
hint:
Here, we only use the Administator account to run individual programs temporarily. To prevent other people from using this account to log in to the system, we can set a very complicated password for us. We only need to use this password once.
Right-click on the desktop blank, select "New Shortcut", type "C:\Windows\System32unas.exe /user:administrator /savecred cmd" in the type object box, run the command prompt as Administrator (if you want to run For other programs, please change the program name yourself. Also use /savecred to save the password for the Administrator account and name the shortcut "command prompt" (Figure 2).
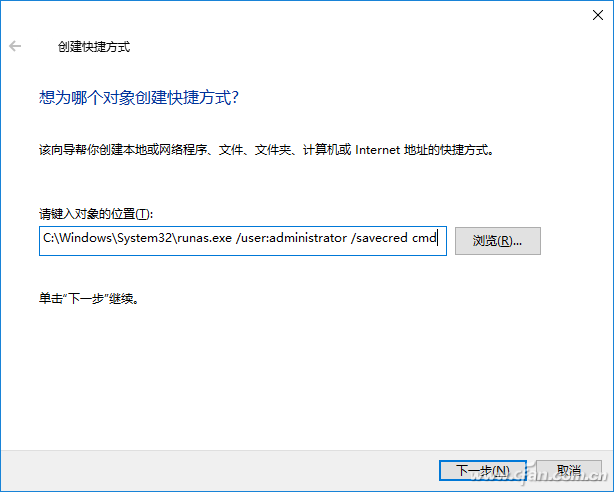
Figure 2 Creating a Shortcut
In this case, when we need to run the command prompt as an administrator, just run the above new shortcut on the desktop (the first time you need to enter the password of the Administrator account, do not enter it later) so that you can bypass the UAC interception and start the command prompt directly as the Administrator. Character (Figure 3).
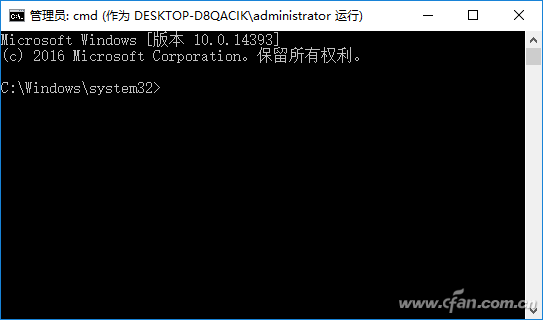
Figure 3 Starting the Command Prompt as Administrator
Change browser to bypass system account limit
Use tools: 7ZIP
For important system directories such as c:ecovery, only the system built-in SYSTEM account has read access by default. Even if we log in as an administrator and try to access it, the system will prompt you to reject the access because the current account does not read the directory. Permissions (Figure 4).
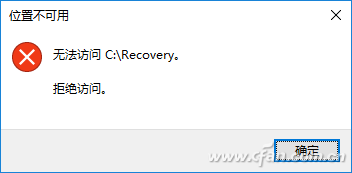
Figure 4 Cannot Access System Protection Directory by Default
The usual solution is to first obtain the ownership of the directory, and then set the current account full control of the directory, only in this way can access the directory. However, since Windows 10 sets permissions protection, the purpose is naturally to better protect the system files. It is easier to bring about security risks by artificially changing the owner and permission settings of the system directory. If we just want to temporarily access these directories to copy the files, then use the 7ZIP file manager. Enter "7zip file Manager" in the search box, and then start as administrator. In the browser window, expand C:ecovery as prompted. You can see that the file manager can open the above directory directly, and select the file to be copied when prompted. Right-click to select "Copy to" and select the save location to copy the files (Figure 5). After exiting the 7ZIP file operation, the original permissions of the system directory did not change.
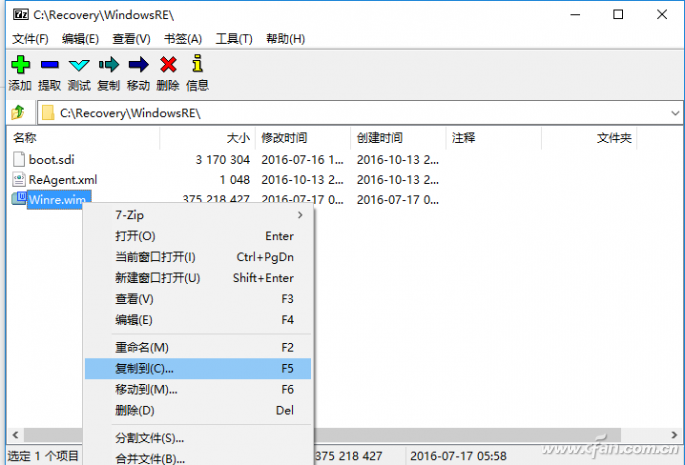
Figure 5 In 7ZIP can open restricted directories
Temporary privilege escalation, easy to change system file name
Use tools: WinOwnership
Except for the system protection directory, the system directory such as the program under C:\windows\system32 has its default owner and control authority only owned by the system's built-in TrustedInstaller account. When we try to delete or rename files, the system It will also pop up the file access denied prompt, always click "Retry" can not complete the operation, but many times there are indeed need to perform a similar operation, such as the need to change the cmd to osk.exe in order to change the login interface to forget the system login Password (Figure 6).
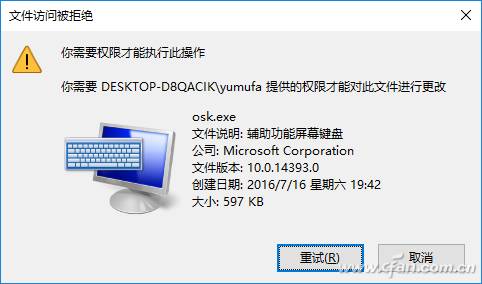
Figure 6 The system file is only fully owned by the TrustedInstaller account.
The usual solution is also to change the file owner and control permissions, so that the operation will also bring security risks. You can now gain full control over Temporyship temporarily. After starting the program, double-click it in the window, and then select the system file that needs to be operated as "C:\windows\system32\osk.exe" and click "apply" to obtain the full control right temporarily (Figure 7).
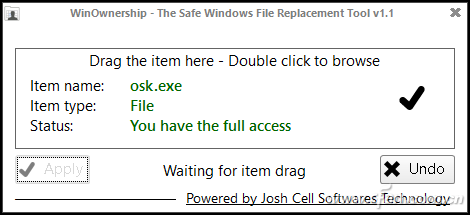
Figure 7 Temporary access permissions
Now open "C:\windows\system32\osk.exe", right-click and select Rename, the system will pop up the need to provide administrative privileges to operate prompts (note that the prompt window has been different), click "continue" to complete the file Rename operation. After completing the operation, return to the program window and click "undo" to cancel the temporarily obtained permission (Figure 8).
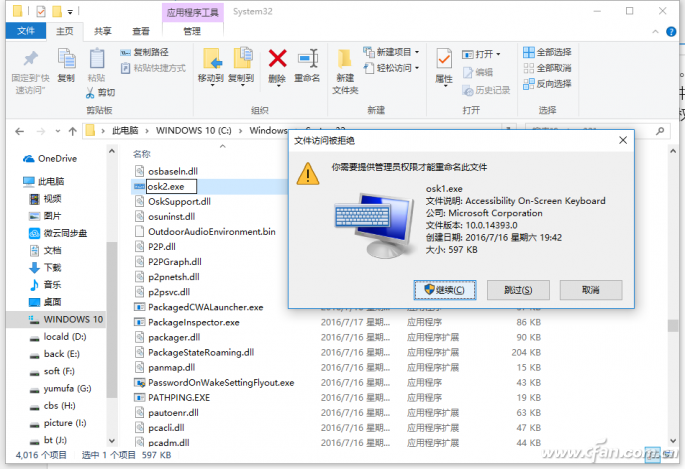
Figure 8 Can Be Performed After Temporarily Acquiring Privileges
High Voltage Inverter For Car,Car Inverter,Power Inverter,High Voltage Inverter
SUZHOU DEVELPOWER ENERGY EQUIPMENT CO.,LTD , https://www.fisoph-power.com