A UDP flood attack is one that causes a host-based service to reject an attack. UDP is a connectionless protocol, and it does not require any program to establish a connection to transfer data. When an attacker randomly sends a UDP packet to the port of the victim system, a UDP flood attack may occur. When the victim system receives a UDP packet, it determines which application the destination port is waiting for. When it finds that there is no waiting application in the port, it will generate an ICMP packet whose destination address cannot be connected and send it to the forged source address. If enough UDP packets are sent to the victim's computer port, the entire system will crash.
UDP flood attack prevention
Using a firewall at a critical point in the network to filter harmful data from unknown sources can effectively mitigate UDP flood attacks. In addition, the following measures should be taken in the user's network:
Disable or filter monitoring and response services.
Disable or filter other UDP services.
If the user must provide external access to some UDP services, then a proxy mechanism is needed to protect that service so that it is not abused.
Monitor your users' networks to see which systems are using them and monitor signs of abuse.
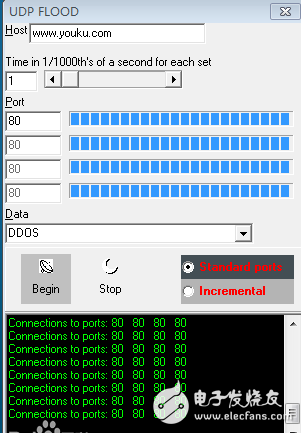
UDPFlood is an increasingly rampant traffic-type DoS attack, and the principle is simple. A common situation is to use a large number of UDP packets to impact DNS servers or Radius authentication servers and streaming video servers. UDPFlood of 100k bps often smashes backbone devices such as firewalls on the line, causing paralysis of the entire network segment. Since the UDP protocol is a connectionless service, in a UDPFLOOD attack, an attacker can send a large number of small UDP packets that spoof the source IP address. However, since the UDP protocol is connectionless, as long as a UDP port is provided to provide related services, attacks can be made against related services.
Under normal application conditions, the UDP packet bidirectional traffic will be basically equal, and the size and content are random and vary greatly. In the case of UDPFlood, UDP packets for the same destination IP appear on a large scale, and the content and size are relatively fixed.
UDPFlood is an increasingly rampant traffic-type DoS attack, and the principle is simple. A common situation is to use a large number of UDP packets to impact DNS servers or Radius authentication servers and streaming video servers. UDPFlood of 100k bps often smashes backbone devices such as firewalls on the line, causing paralysis of the entire network segment. Since the UDP protocol is a connectionless service, in a UDPFLOOD attack, an attacker can send a large number of small UDP packets that spoof the source IP address. However, since the UDP protocol is connectionless, as long as a UDP port is provided to provide related services, attacks can be made against related services.
Under normal application conditions, the UDP packet bidirectional traffic will be basically equal, and the size and content are random and vary greatly. In the case of UDPFlood, UDP packets for the same destination IP appear on a large scale, and the content and size are relatively fixed.
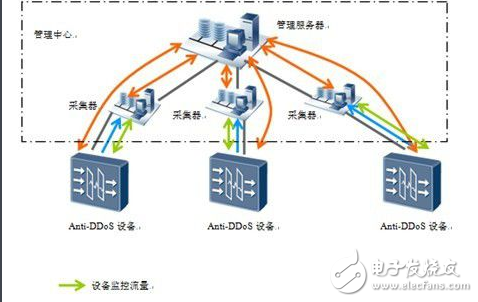
The attacker sends a large number of UDP packets to the target server through the botnet. This UDP packet is usually a large packet and is very fast. This usually causes the following harms. As a result, the server resources are exhausted, the normal request cannot be responded, and the link is congested in severe cases.
The general attack effect is to consume network bandwidth resources, causing link congestion in severe cases.
A large number of UDP floods with variable source ports can cause network devices that rely on session forwarding to degrade performance and even exhaust the session, causing network congestion.
If the attack packet reaches the UDP service port that is open to the server, the server checks the correctness of the packet and consumes computing resources, which affects normal services.
APM DC Source System is a single output programmable smps power supply which provides with high power density and stable DC output. The dc switching power supply offers continuously variable output voltage and current for a broad range of applications.
Some features as below:
- With accurate voltage and current measurement capability.
- Coded Knob, multifunctional keyboard.
- Standard RS232/RS485/USB/LAN communication interfaces, GPIB is optional.
- Remote sensing line voltage drop compensation.
- Equips with LIST waveform editing function.
- Use the Standard Commands for Programmable Instrumentation(SCPI) communication protocol.
- Have obtained CE certification.
200V DC Source System,High Power Power Supply,Current Dc Power Source,Dc Led Power Source
APM Technologies Ltd , https://www.apmpowersupply.com